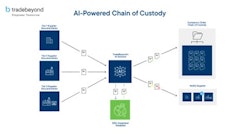
Although food safety and security is better today than ever before, it seems every step forward is offset by a new set of vulnerabilities—some of these are related to growing supply chain complexities, while others are the result of tampering or cargo theft.
Food Logistics checked in with industry experts to get their perspective on where the risks lie and how they can be mitigated, starting with food safety…
Don Hsieh, director of commercial and industrial marketing for Tyco Integrated Security acknowledges the proliferation of risk associated with an increasingly global food supply chain.
“The biggest risk to food safety in the global food chain are the multiple points of vulnerability directly related to the complexity and length of the supply chain,” he says. “In the U.S. alone, there are approximately 2 million farms that produce food; over 400,000 food facilities that process or distribute food that are registered with the FDA, of which over 60 percent are foreign facilities; millions of containers of food are moved on trucks, trains and ships every year; and ultimately food is distributed to over a million points of sale, such as restaurants, grocery stores and other food service outlets.”
Managing risk is this environment has become more challenging due to increased food imports, says Hsieh. For example, “the U.S. imports about 20 percent of the food we eat, and that ratio is even higher in some categories,” he says, such as seafood imports, which run as high as 80 percent, and fruits and vegetables, which are in the 50 percent range. “Even a simple loaf of bread can contain ingredients that come from 14 countries,” Hsieh points out.
“Every node in this global food chain is a potential point of vulnerability for unintentional or intentional food adulteration, and to quote an oft used phrase, ‘The global food chain is only as strong as the weakest link.’”
According to Hsieh, “ It is incumbent on every player in the food chain—from suppliers, manufacturers, distributors and retailers—to implement a proactive food defense program to help prevent food adulteration; first and foremost to protect the safety and health of the consumer, as well as protect the reputation of the brands that consumers trust.”
Of course, the Food Safety Modernization Act (FSMA) is helping drive action on this front, he says. “The focus of FSMA is on implementing preventive controls to protect against foodborne disease from both intentional and unintentional sources. The law, for the first time, now clearly requires companies to implement a food defense program.”
When it comes to food defense strategies, Hsieh offers this advice: “It is imperative that food and beverage manufacturers and distributors develop a proactive food defense program that delivers comprehensive control over the integrity of their supply chain to combat food adulteration. Implementing preventive and proactive controls built on actionable intelligence to protect the food supply chain is significantly more effective than reacting to an adulteration event after it happens. The benefits of a strong food defense strategy include increasing consumer safety, reducing operational risks and protecting brand reputation.”
Hsieh suggests using “the Four A’s” of food defense as the core components of a proactive food defense program:
• Assess: Vulnerability assessment of critical control points
• Access: Allow only authorized staff access to critical control points
• Alert: Continuously monitor the whole supply chain to alert appropriate individuals of intentional and unintentional instances of food adulteration
• Audit: Determine operational and regulatory compliance to best food defense practices and provide documentation of compliance to regulators
Glenn Pogust, litigation partner at law firm Kaye Scholer, agrees that more food imports are fueling food safety concerns. “As the volume and variety of imported food products continues to rise, especially from an increasingly broad number of foreign sources, the potential for imported food products to be the cause of contamination or other forms of injury will also expand,” he cautions. “Because domestically-based importers are likely the only viable targets in the event of U.S.-based injury litigation, those importers should utilize all risk management tools reasonably available to them both with respect to their foreign suppliers and with respect to all aspects of storage and transportation of their products to the ultimate user.”
On Friday, May 20, 2011, a tractor-trailer pulled into a cold-storage warehouse in Los Angeles and picked up a load of Russian king crab. The driver was expected to deliver his cargo in Seattle the following Monday. Instead, he vanished—along with some 25,000 pounds of king crab with an estimated wholesale value of $400,000. The last anyone heard from the driver was on the Monday, when he called, supposedly from Oregon, to report that his vehicle was having mechanical trouble. In its frantic search for the freight, the load broker discovered that the driver’s contact information, documents, and his trucking company all were bogus, fashioned by a well-organized fraud ring.
Identity theft—assuming a legitimate carrier’s identity so thieves can schedule appointments and pick up freight—is among the fastest-growing types of cargo-related crime. While two out of three reported cargo thefts occur at unsecured parking areas, identity-related cargo theft is designed to give thieves access to secured yards and distribution centers, where the most valuable products are.
“This type of crime is frustrating and hard to detect because the transaction looks legit from the get-go,” says Jeff Hall, a private investigator and principal with Transit Risk Management in Dallas. “You or your load broker or 3PL hire a carrier to haul your freight, he arrives at your dock on time, his papers seem in order, and then he sits there while you fill his trailer with the stuff he’s going to steal.”
After he pulls away, the driver might check in with the broker once or twice to say everything is fine, and then the next call is from the receiver wondering where the truck is. When the broker tries to contact the driver or carrier, he ultimately learns that he’s calling a throwaway phone and writing to a bad email address. The broker is left to ask what did he really know about that carrier when he brokered the load?
Mitigating the risks
Identity-related cargo theft is more prevalent on the spot freight market and commercial load boards without the tools and data to help shippers and brokers verify carrier credentials as part of their due diligence.
“The very nature of the spot market is that shippers, brokers, and 3PLs need immediate available truck capacity,” says Michele Greene, group product manager at DAT, North America’s largest electronic load board network. “At the same time, there are new carriers and independent owner-operators who use commercial load boards as a place to establish relationships with brokers and 3PLs.”
Like any matching service where people initially meet online, you want to do your due diligence before you get together in person. While there’s no way to guarantee protection against identity-related cargo theft, you can mitigate the risk by carefully screening the carriers with whom you do business. Here are six steps you can take:
Step #1 Identify “Risky” Loads
The riskiest load isn’t necessarily the one with the highest value. Hall explains why:
Rather than take cargo for their own use, thieves typically resell stolen goods, using the money to fund other illegal activities. “The truck driver probably won’t know what he’s moving until later when he cracks open the trailer,” he says.
So thieves will look for clues based on routine information supplied by the broker when he posts the load: the type of trailer needed, the origin and destination of the load, insurance requirements, the urgency of the load, and so on.
“They’ll look for a long-haul load that’s going to take two to four days in transit, or a load they can pick up on a Friday, so there’s time before anyone suspects a problem,” Hall explains. “They’ll look for a last-second load or an expedited load or one that requires team drivers. They’re not necessarily targeting the high-dollar load. They’re taking advantage of people who are in a hurry and not paying close attention.”
Step #2 Put Load Board Tools
to Work
Thieves typically use publicly available information about a carrier—one that’s either in business or defunct—to build a false identity. Their tactics can be remarkably simple: if a bad guy sees that “Quality Trucking” is a carrier you know well, he might set up shop as “Quality Trucking Express,” complete with a phone number and web domain that’s just close enough to fool you into tendering a load.
When a carrier makes initial contact with you, look at its caller ID. If necessary, verify its authenticity with a return phone call to the phone number listed by the FMCSA, and ask to speak with your contact by name so you know he or she works there.
Load boards can facilitate best practices in carrier qualification in two ways: by verifying the credentials of all participants, ensuring that they are legitimate businesses; and by providing load board customers with the tools and data they need to pursue their own due diligence procedures comprehensively, quickly, and efficiently.
“If you use a load board, ask what data is available to help verify that the person you’re dealing with is a bona fide representative of the carrier,” Greene says. DAT, which facilitates more that 88 million freight transactions a year, maintains the DAT Directory, a repository of carrier information including DOT authority, CSA safety ratings, insurance coverage, and current contact information. Brokers and shippers search the DAT Directory more than 500,000 times per month (or more than 16,000 times every day) in their efforts to verify that carriers are properly credentialed.
“Load boards collect a tremendous amount of information that can help shippers and brokers verify that a carrier is a legitimate business,” Greene says. “Ask what’s available and put that information to use.”
Step #3 Verify Insurance
Insist on an insurance certificate directly from the insurance agent, not the carrier, and verify that the agent is legitimate. Use a reverse phone lookup to check that the agent’s phone/fax number actually belongs to an insurance agent, not an accomplice posing as one. Better yet, use a third-party service to verify insurance, or ask your load board what it can do for you. For example, DAT offers a service called CarrierWatch where brokers can view and/or download digital images of insurance certificates verified by carriers’ insurance providers; Greene says more than half of DAT’s broker customers now use the service to confirm coverage details.
Step #4 Check the MC Number
The vast majority of new carriers are legitimate, but check business references and be especially vigilant with carriers that have a brand new operating authority (Motor Carrier Numbers beginning with “7”). Companies that ditch their old authority and start with a clean slate under a new MC number are known as “chameleon” carriers. “I was investigating a cargo theft case and the carrier involved shared an address with no fewer than 148 other MC and MX numbers, as well as a registration and insurance service,” says Greene.
Step #5 Meet the Driver
Ask the driver directly for the name and number on the side of the truck and verify that he is employed by the carrier you hired.
“I’ve had victims of identity-related cargo theft say to me that everything looked good on paper but something was ‘off‘ with the driver or the equipment,” Hall says. “I had one where someone stole the identity of a very well-known truckload carrier and showed up with a flatbed trailer to pick up a load of tablet computers. The guys at the dock loaded him up because, well, he had all his papers.”
Step #6 Develop an Action Plan
Thieves gain valuable time when shippers and brokers don’t have a procedure for reporting stolen goods. Who makes the call that a load is stolen? Is it the shipper whose cargo is missing, or the load broker who booked the carrier?
Hall says calling the local police is a start, but typically they’re not experts in cargo theft and don’t know how to proceed with an investigation.
“They send a patrolman out to investigate: Did the thieves break in? No, they backed up to the dock and the guys in the warehouse loaded up 22 pallets of salmon onto the trailer. So it was an inside job? No, the truck driver took it. At what point during the trip did the truck driver decide to steal the load? We don’t know, he was using a fake identity. I don’t mean to be disrespectful, but most local law enforcement aren’t trained to handle this sort of thing.”
Hall recommends speaking with your insurance carrier to develop a comprehensive plan for reporting and investigating cargo theft, and identity-related theft in particular. “This is not an inside job and it’s not a grab-and-dash type of theft,” he explains. “Identity theft is typically well organized and takes advantage of the way you manage your due diligence and business relationships.”
No amount of diligence can guarantee protection against cargo theft, but a few extra minutes spent validating a carrier, using a combination of technology and common sense, can help you minimize your risk.
Kevin Scullin is a product manager with DAT in Portland, OR.
In his executive summary, Cmdr. Kramek stated that: “Today, U.S. port facilities rely as much upon networked computer and control systems as they do upon stevedores to ensure the flow of maritime commerce that the economy, homeland, and national security depend upon. Yet, unlike other sectors of critical infrastructure, little attention has been paid to the networked systems that undergird port operations. No cybersecurity standards have been promulgated for U.S. ports, nor has the U.S. Coast Guard, the lead federal agency for maritime security, been granted cybersecurity authorities to regulate ports or other areas of maritime critical infrastructure. In the midst of this lacuna of authority is a sobering fact: according to the most recent National Intelligence Estimate (NIE) the next terrorist attack on U.S. Critical Infrastructure and Key Resources (CIKR) is just as likely to be a cyber attack as a kinetic attack.”
Indeed, Cmdr. Kramek says awareness about cyber attacks is virtually nil. He writes in the report that: “The Coast Guard’s current port security authorities empower them to enforce the physical security provisions required by the Maritime Transportation Security Act (MTSA)—a statute passed in the wake of the 9/11 attacks that was designed to protect U.S. maritime critical infrastructure against kinetic terrorist attacks.”
However, “MTSA does not contain any cybersecurity requirements, nor do any of the 13 major regulations predicated upon it. Rather, MTSA’s requirements can loosely be summed up as guns, gates, guards, and identification cards. Since the Coast Guard focuses on holding port facilities accountable for compliance with MTSA’s physical security requirements, it is no surprise that port facility owners and operators also focus on physical security and not cybersecurity.”
Not everyone agreed with his findings, including the Port of Long Beach, which told the Los Angeles Times that, “We have the latest cybersecurity technologies. We patch all of our systems on a regular basis. We continuously train our users on cybersecurity best practices.”
The Port of Baltimore went further, stating that, “In a nutshell, we feel this is a very misleading report.”
What would likely be agreed upon, however, is the level of impact a cyber attack could potentially unleash.
Cmdr. Kramek warns: “The potential consequences of even a minimal disruption of the flow of goods in U.S. ports would be high. The zero-inventory, just-in-time delivery system that sustains the flow of U.S. commerce would grind to a halt in a matter of days; shelves at grocery stores and gas tanks at service stations would run empty. In certain ports, a cyber disruption affecting energy supplies would likely send not just a ripple but a shockwave through the U.S. and even global economy.”
He cites last November’s impact of Hurricane Sandy, which “caused severe damage in the Ports of New York and New Jersey, preventing shipments of petroleum from being offloaded and trucked from ports to filling stations.”
Cmdr. Kramek adds, “Tanks at gas stations across the region quickly ran dry. In just days, residents relying on gasoline generators for heat and power began to panic. In another incident in 2012, labor strikes in the Port of Los Angeles-Long Beach forced ships to remain offshore, shutting down terminal operations, and causing truckers and rail cars to back up outside port entrances, resulting in an economic impact of $1 billion per day in lost wages, business revenue, and the value of cargo that had to be diverted to other ports.”
Furthermore, he says that of the six ports he researched, only one (the Port of Long Beach) had undertaken a cybersecurity vulnerability assessment and none had a cyber incident response plan.
“Moreover, of the $2.6 billion allocated to the U.S. Port Security Grant Program—created in the wake of 9/11 to fund new congressionally mandated security requirements at U.S. ports—to date, less than $6 million has been awarded for cybersecurity projects,” concluded Cmdr. Kramek. ?